Executive Summary
UN Regulation No. 155 (UNR 155) has shifted automotive cybersecurity from an optional feature to a mandatory requirement for vehicle type approval. However, true compliance is not merely about documentation; it requires a fundamental shift in Electrical/Electronic (E/E) architecture.
This whitepaper details x18 Technology’s “First-Principles” approach to implementing a robust Cyber Security Management System (CSMS). We move beyond theoretical compliance to address practical engineering challenges, dissecting attack vectors from the ECU firmware level up to telematics protocols.
Key Technical Insights
This document covers the following technical implementations:
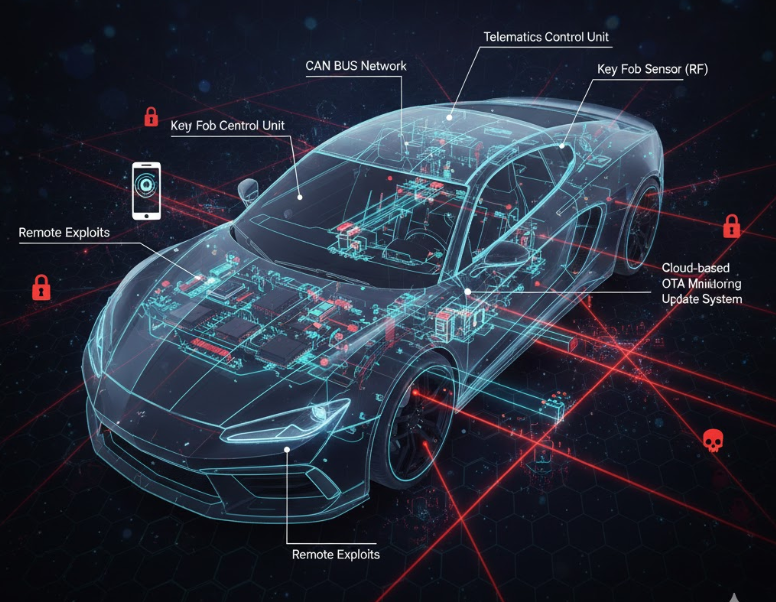
- Attack Surface Mapping: Deconstructing vulnerabilities inherent in legacy CAN bus protocols and securing the pipeline for OTA (Over-the-Air) updates.
- Distributed IDS: deploying Intrusion Detection Systems directly at the Gateway and Domain Controller levels to identify anomalous traffic patterns and spoofing attempts in real-time.
- Hardware Root of Trust: Utilizing Hardware Security Modules (HSM) to enforce secure boot sequences and digital signature verification before kernel initialization.
Architecture Overview
We advocate for a Defense-in-Depth strategy, structured around three critical layers of protection:
- Perimeter Defense: Telematics Unit firewalls and API security gateways.
- Network Security: Strict network segmentation and whitelist-based CAN message filtering.
- Endpoint Hardening: OS hardening and runtime integrity checks for individual ECUs.
Intended Audience
- Automotive Systems Architects
- Cybersecurity Engineers
- ISO/SAE 21434 Compliance Officers



